Wiper in Ukraine Used Code Repurposed From WhiteBlackCrypt Ransomware
This month's wiper attack against government agencies in Ukraine has been tied to a 2021 ransomware campaign and a 2019 extortion plot against a Russian oligarch, investigators say.

The code used in the WhisperGate wiper that targeted government agencies in Ukraine this month was re-purposed from a ransomware campaign that targeted Russian victims last year, according to Ukrainian investigators who analyzed the code.
The WhisperGate wiper masqueraded as ransomware while performing its real purpose — to destroy files on dozens of systems in two Ukrainian government agencies in order to render those systems inoperable.
Now it appears that the WhisperGate code was modified code from a different faux ransomware campaign discovered last year called WhiteBlackCrypt. Like WhisperGate, WhiteBlackCrypt masqueraded as ransomware but actually had a wiper component to erase systems. It targeted Russian victims says Victor Zhora, deputy director of Ukraine's State Services for Special Communication and Information Protection, which published an announcement about the new findings today.
Zhora says the actors behind WhisperGate may have used the WhiteBlackCrypt code in an attempt to falsely point the finger at Ukraine — that is, to make it appear that Ukraine was itself responsible for the infections that destroyed its government systems this month.
“They simply modified the WhiteBlackCrypt malware that was used in a provocative fashion against Russia two years ago,” says Zhora, “and the idea was to potentially attribute the [WhisperGate] wiper to Ukrainians.”
But the two campaigns have more in common than just code. Both false ransomware campaigns instructed victims to send payment to the same cryptocurrency wallet. Furthermore, that wallet was also used in another operation that occurred in 2019 — this one involving bomb threats made against buildings in Russia in an attempt to extort a Russian oligarch named Konstantin Malofeev.
Microsoft confirmed that the WhisperGate wiper shares some elements with WhiteBlackCrypt.
“Microsoft…can confirm that several elements of the malware code have logical overlaps with commodity components from other ecosystems. This includes a shared crypter/downloader and the final WhisperGate file corruption utility, that has logical/semantic overlaps with WhiteBlackCrypt,” a company spokesperson said in an email, adding that “due to the disguised and possibly complex nature of the intrusion activity, we encourage caution regarding any conclusions to allow time for investigators to carry out a thorough and accurate investigation.”
The story is a bit complicated, so Iet’s unpack it.
In 2019, for nearly a month, unknown actors made thousands of bomb threats against courts, hospitals, shopping malls, schools, transportation hubs and media outlets in Russia, forcing evacuations at sites across the country. The perpetrators demanded that Russian oligarch Konstantin Malofeev pay 120 in Bitcoin (about $870,000 at the time) to prevent the bombs from going off.
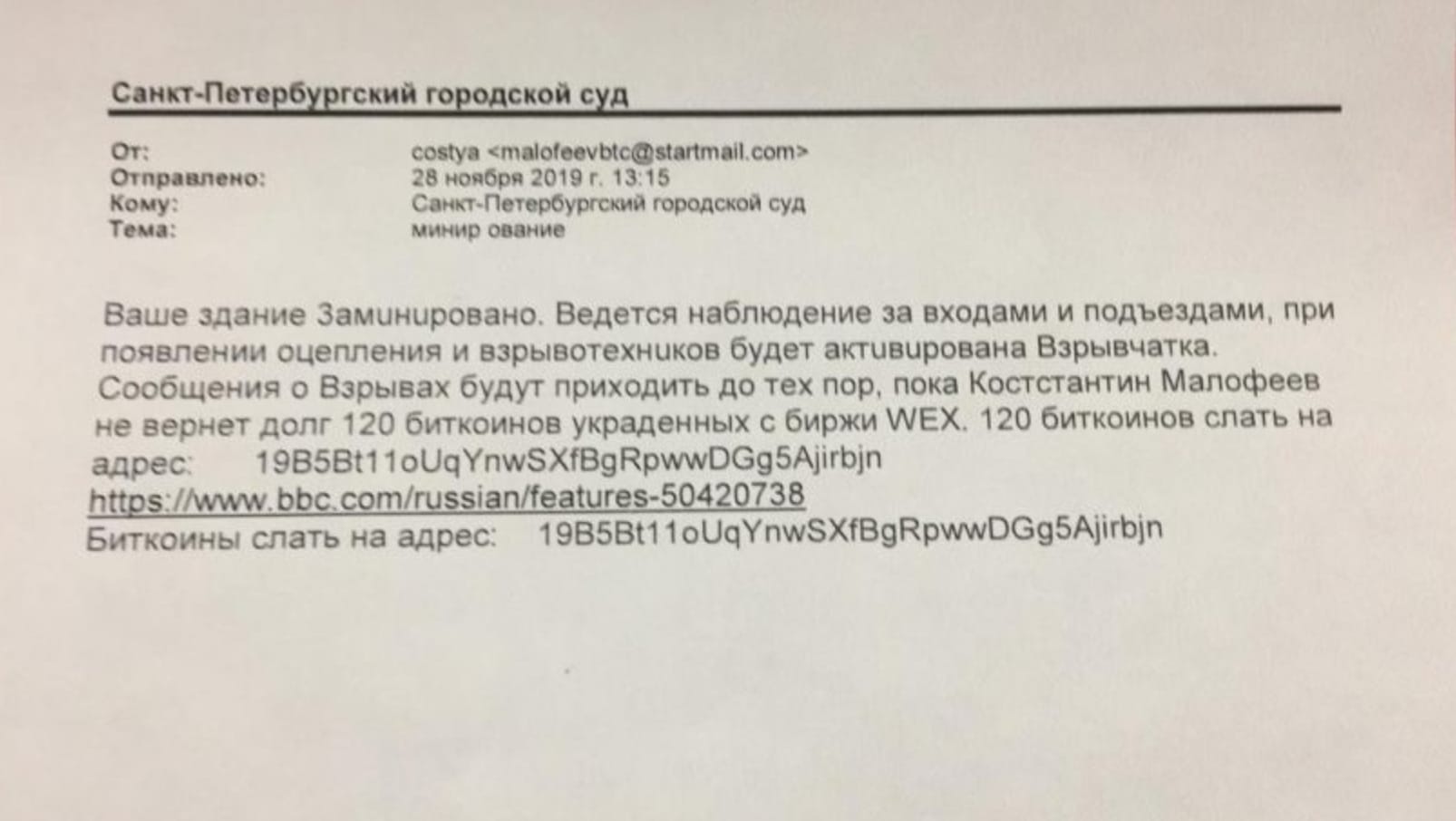
The actors blamed Malofeev and Anton Nemkin, a former officer of Russia’s Federal Security Service (FSB) for allegedly stealing $450 million in cryptocurrency from the now-defunct Russian cryptocurrency exchange WEX. Alexei Bilyuchenko, the alleged administrator of WEX, claimed that two FSB officers had forced him to hand over all the exchange’s cryptocurrency and also demanded the database of WEX users.
No bombs went off, but a small amount of cryptocurrency did get sent to the wallet address the perpetrators used in their extortion demand. From there some of it got transferred to other wallets, including one purportedly controlled by a hacker group going by the name Encrpt3d and a wallet rumored to be controlled by a division of Ukraine’s special forces — though Zhora says the division they named in the extortion demands doesn’t exist as far as he knows. No proof has ever been provided that Ukrainian forces control the wallet, but Zhora says this was likely meant to implicate Ukraine in the extortion and bomb threats.
In the spring of 2021, a ransomware campaign came to light called WhiteBlackCrypt, which Microsoft detected at the time. Zhora says the wallet used in this campaign was the same wallet used in the bomb threat extortion campaign, and that the ransomware message included a trident symbol that is part of Ukraine’s coat of arms.


Zhora says that WhiteBlackCrypt targeted “random victims, mostly Russian,” according to his sources, and that the fake ransomware was really a cover for a wiper attack aimed at destroying infected computers.
Then this month, when unknown actors launched web site defacements and wiper attacks against Ukrainian government agencies, they used re-purposed code from the WhiteBlackCrypt campaign as well as the same cryptocurrency wallet — though the actual text of the ransomware message posted on Ukrainian government web sites this month appeared to be an attempt at a false flag operation blaming Poland for the campaign.
Zhora says he thinks the actors may have intended to do more to point the finger at Ukraine but changed their minds. In any case, he believes they re-used the code and the cryptocurrency wallet for the operations against Ukraine this month knowing that investigators who analyzed the WhisperGate wiper would notice the links to the previous WhiteBlackCrypt campaign and the bomb threats against the Russian oligarch.
“That was their intention — to put a false flag to Ukrainians and to show that Ukrainians could potentially attack their own infrastructure,” he told Zero Day. “I believe that was one of the ideas and I’m curious why they didn’t use [the trident in the WhisperGate operation].”
No one has taken credit for the web site defacements and the WhisperGate wiper this month, and Zhora says that investigators still are not ready to make a formal attribution to any actor or country — even though some Ukrainian officials have pointed the finger at Belarus and Russia.
Update 1.27.21: To add comment from Microsoft confirming that WhisperGate and WhiteBlackCrypt share some elements.
Related:
What We Know and Don’t Know about the Cyberattacks Against Ukraine - (updated)
Dozens of Computers in Ukraine Wiped with Destructive Malware in Coordinated Attack
Hackers Were in Ukraine Systems Months Before Deploying Wiper
Inside the Cunning, Unprecedented Hack of Ukraine’s Power Grid
The Ukrainian Power Grid Was Hacked Agai
If you like this story, feel free to share with others.
If you’d like to receive future articles directly to your email in-box, you can also subscribe: