Updates and Timeline for 3CX and X_Trader Hacks
Mandiant revealed this week that the hack of 3CX was actually a double supply-chain hack that first involved hacking and compromising another company's software. Here's a timeline of the events.
I’ve added a number of updates with new information to the story I published this week about the double supply-chain hack of 3CX VoIP software and Trading Technologies’ X_Trader financial trading program. You can read them all at this link.
Additionally, I thought it might be helpful to provide a timeline here (which I’ll update as the investigation unfolds).
The telephony company 3CX makes a popular VoIP software — Electron Desktop Application — for live chat, video conferencing and voice calls that is used by more than 600,000 organizations in 190 countries. Among its customers are AirFrance, American Express, BMW, ClubMed, Holiday Inn, McDonald’s, Toyota, and the National Health Service in the UK.
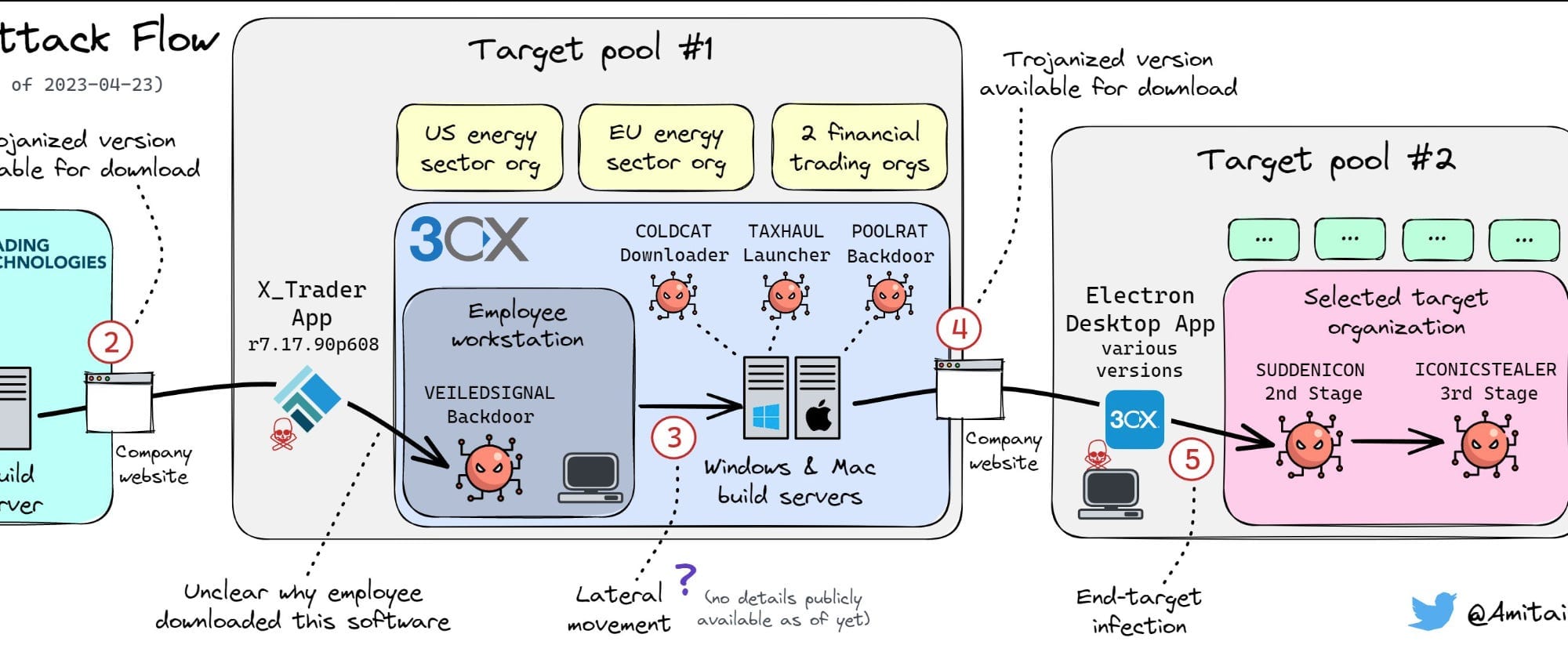
On March 30th, the company revealed that several versions of its VoIP application had been compromised with malicious code that got distributed to customers. An investigation found that the breach didn’t begin with 3CX, however, but began in 2021 when the hackers first compromised a different software company — Trading Technologies — and slipped a malicious backdoor into versions of that company’s X_Trader software program.
Mandiant has called it the first known case of a double supply-chain hack. “This is the first time that we’ve ever found concrete evidence of a software supply-chain attack leading to another software supply-chain attack,” Charles Carmakal, CTO of Mandiant’s consulting group, said. “This is very big and very significant to us.”
Mandiant, Kaspersky, ESET and other security firms have attributed the hacks to financially motivated state-sponsored actors from North Korea. Kaspersky and ESET specifically connect it to the North Korean hacking group known as Lazarus. Here’s what is known so far:
2018
September 2018 - Trading Technologies announces to customers that it will be de-commissioning its futurs trading X_Trader software in 18 months, at which point it will no longer provide support for the product. The software, according to the company, is a niche program used primarily by banks and their customers to do futures trading, including energy futures.
2020
April 2020 - Trading Technologies de-commissions X_Trader.
2021
November 2021 - at an unknown time in 2021, hackers working for North Korea breach the network of Trading Technologies. In November, the hackers use a Trading Technologies digital certificate to sign compromised versions of the X_Trader software. Shortly after this, the compromised software is made available on the Trading Technologies web site for download. It’s unclear how the hackers embedded the malware into the software and signed it with the digital certificate, but in 2020 hackers from Russia compromised the software build server of a company called SolarWinds to do embed malware in one of its programs, and it’s possible the North Korean hackers copied this technique. If the North Korean hackers used Trading Technologies’ own build server to compile and sign the software, it’s not clear how the company failed to notice or detect when a software it no longer developed was being compiled on its servers more than a year after it decommissioned the program.
2022
November 2021 to August 2022 - the tainted X_Trader software remains on the Trading Technologies site until August 2022, during which an unknown number of people download the compromised program. They download it even though the software is defunct and no longer supported by Trading Technologies. The company says 97 people downloaded the software. All of them downloaded the program between November 1, 2021 and July 26, 2022.
February 2022 - Google’s Threat Analysis Group (TAG) reveals that North Korean hackers have compromised Trading Technologies' web site — www.tradingtechnologies[.]com — and planted hidden exploit code on it to infect visitors to the site. The TAG team evidently is unaware that at the same time the site is also serving tainted versions of the X_Trader software to anyone who downloads that program and has begun to register “a sprawling set of infrastructure” to use on their operation, according to SentinelLabs, Sentinel One’s research arm.
Date unknown, 2022 - At some point before August 2022, an employee of 3CX downloads the tainted X_Trader software to his personal computer. The attackers have full administrator and system-level rights over the computer and steal the employee’s 3CX work credentials, which give them administrator-level access to 3CX’s system as well.
September - November 2022 - At least four customers of the security firm Symantec install the tainted X_Trader software during this time period — the four include two organizations in the energy sector (one in the US and one in Europe, and two in the financial trading industry). Because the X_Trader software is only on the Trading Technologies web site until August, the timeframe suggests the Symantec customers downloaded it before the end of August but don’t install it until one to three months later.
2023
March 2023 - It’s not clear what, if anything, the hackers do on the networks of others who download the X_Trader software, but on the 3CX network we know that they gain access two build servers the company uses for compiling and signing Windows and MacOS versions of its VoIP software. They used this access to slip a backdoor into various versions of the VoIP application. At some point during March, the tainted 3CX software is made available on the 3CX web site, and customers begin to download it.
March 29 - Multiple security firms — CrowdStrike, SentinelOne, Sophos — publish announcements indicating that a component of the 3CX software is compromised. SentinelOne dubs the hacking campaign “SmoothOperator."
March 30 - 3CX reveals that it was hacked and that a compromised version of its software went out to an unknown number of its thousands of customers. A few days later, Kaspersky reports that the hackers appear to have focused on only a small subset of infected 3CX customers, targeting them with additional malware. Among the subset of victims the hackers target are cryptocurrency firms, which suggests they are after financial gain. There’s no evidence they succeeded in stealing cryptocurrency before the operation is exposed.
Update 4.22.23: To provide the exact number of people who downloaded the X_Trader software. The company originally told Zero Day the number was “fewer than 100” but when asked for a firm number indicated that it had confirmed that 97 downloaded it.
Correction: the timeline initially said Trading Technologies first informed customers in early 2019 that it would de-commission X_Trader in 2020. The company actually began telling customers this in September 2018.`
Update 4.23.23: To add information about the threat actor registering infrastructure in February 2022 and to note when security firms first revealed publicly that the 3CX software had a backdoor embedded in it.
If you found this article useful or interesting, feel free to share it with others.
If you’d like to receive future articles directly to your email in-box, you can subscribe for free or become a paid subscriber to help support my work if you find it valuable:
Or if you’d like to give a gift subscription to someone else: