Radiation Spikes at Chernobyl: A Mystery Few Seem Interested in Solving
Ever since radiation sensors at the Chernobyl nuclear plant spiked dramatically following the Russian invasion, there have been questions about what caused the spikes. Now the mystery deepens.
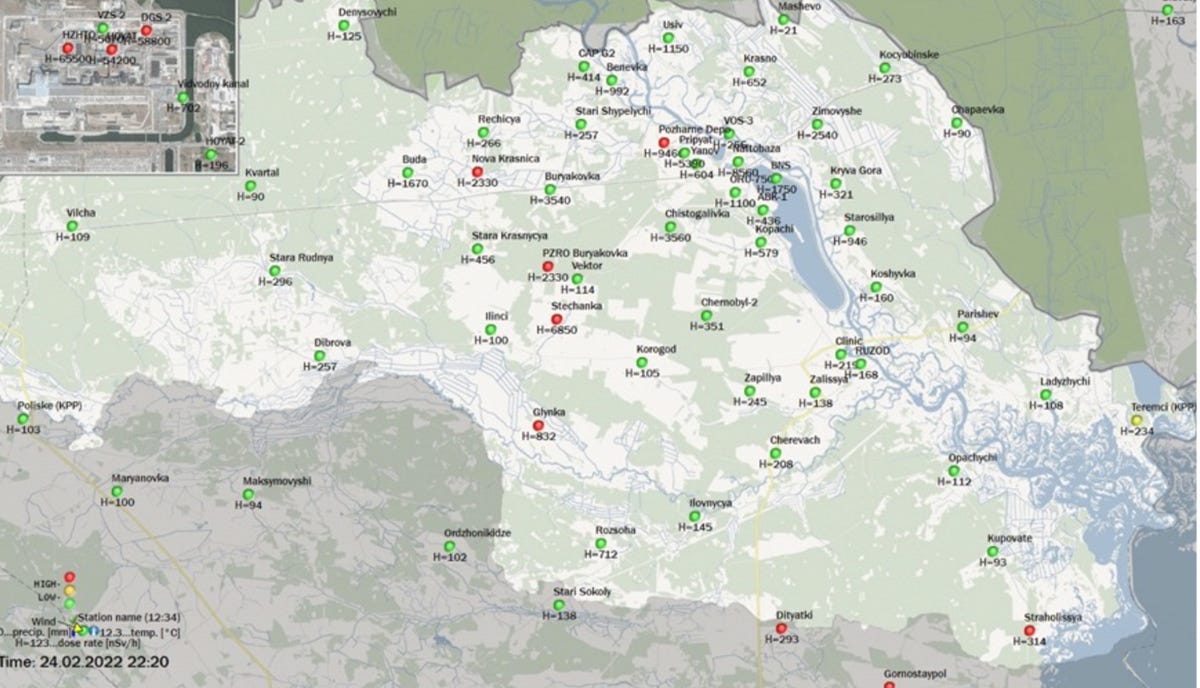
Shortly after Russian troops seized control of the Chernobyl nuclear power plant following the invasion of Ukraine last year, more than forty radiation sensors positioned in the 1,000-square-mile forested area around the plant — known as the Chernobyl Exclusion Zone (CEZ) — began reporting alarming spikes in radiation levels. Ukrainian authorities attributed it to heavy military equipment that they said was stirring up radioactive dirt that had settled in the ground following the 1986 nuclear accident at the plant and condemned Russia for creating a scenario that posed a radiological risk not only to Ukraine but also to Europe.

As I reported in a story for WIRED published yesterday, that explanation didn’t wash with a number of experts I spoke with, including security researcher Ruben Santamarta. After a group of scientists in the United Kingdom published a paper last year discounting the soil theory, someone approached Santamarta about whether it was possible the sensors had been hacked.
A few years ago, Santamarta found unpatched vulnerabilities in radiation sensors (different from the ones used at Chernobyl), that could have allowed someone to manipulate data recorded by the sensors. Intrigued by the mystery at Chernobyl, Santamarta wondered if the Chernobyl sensors might have been vulnerable in similar ways. He spent months last year studying the history of Chernobyl, digging deeply into the technology behind radiation sensors in general and more specifically the equipment setup in the CEZ, and eliminated a number of theories about what might have caused the spikes, before concluding that the data was likely manipulated.
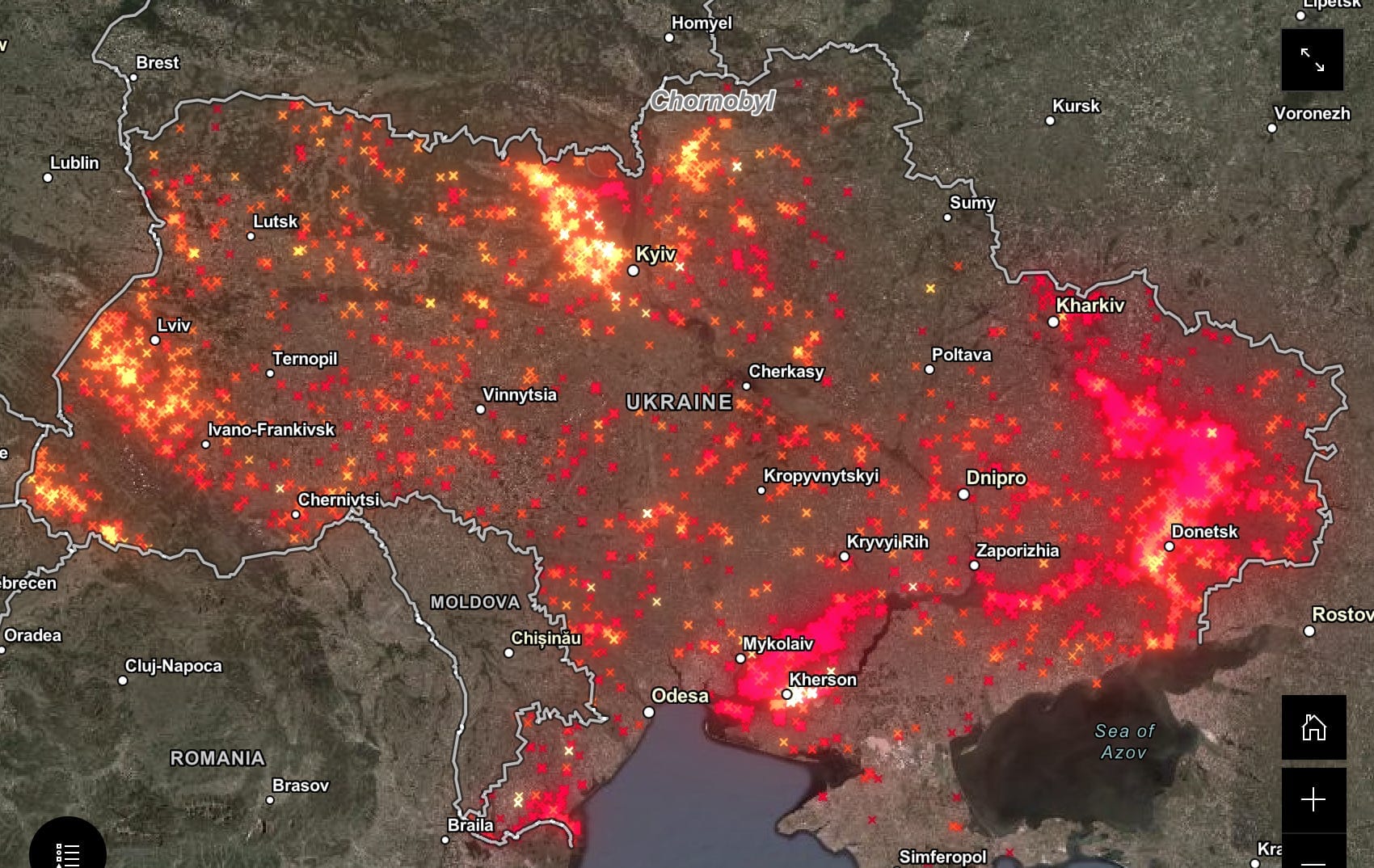
The key was a database he obtained that contained the raw data transmitted by the sensors before, during and after the invasion. Examining this data, which included timestamps indicating exactly when each sensor recorded a spike, he discovered very distinct and suspicious patterns to the spikes.
- They occurred in clusters between 8:40 pm the night of February 24 and 10:50 am the next morning.
- The spike clusters often involved 7, 9, or 11 sensors all spiking at the same time, before dropping back to normal radiation levels within 30 minutes to two hours after a spike.
- Most significantly, sensors that spiked simultaneously were miles away from one another, while sensors closer to them showed no spike at all.
These and other patterns he found in the data didn’t match anything resembling what should occur if the spikes were caused by an actual increase in radiation levels. The patterns led him to conclude that the data was likely manipulated — either by a remote hacker or someone with direct access to the server that processed the data.
I’d recommend reading the WIRED story to learn everything Santamarta uncovered and, if you’re at the BlackHat security conference this week in Las Vegas, Santamarta will be giving a presentation about his findings on Thursday, August 10. He’ll also release a 100-page paper laying out his detailed research.

But in the meantime, I’d like to highlight a few things that I was only able to briefly cover in the WIRED story. You should probably read the story first to understand the context for what I’m going to discuss here.
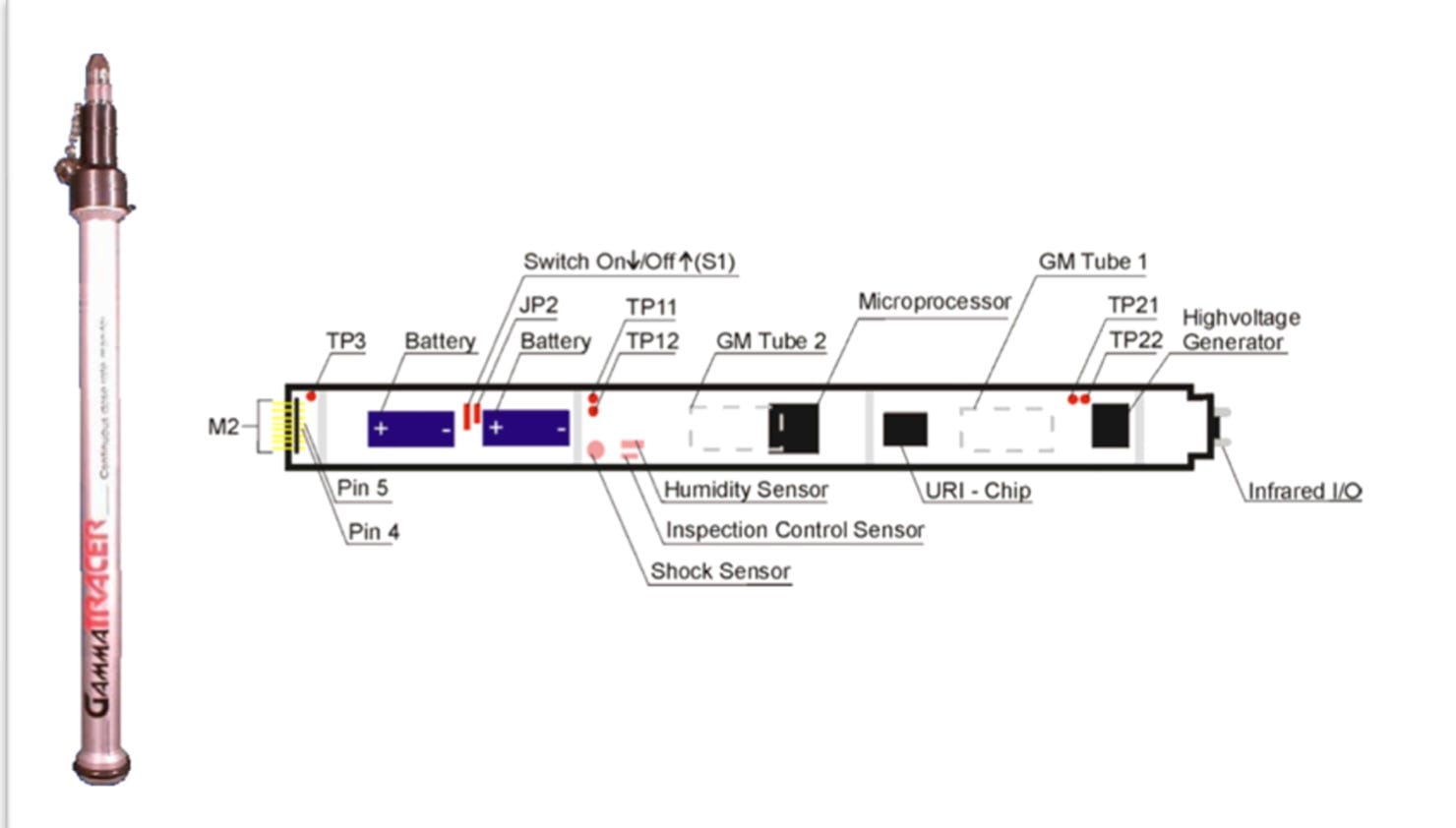
There are about 68 battery-powered radiation sensors at Chernobyl, called GammaTRACERs, that are spread throughout the CEZ. They’re managed by the State Specialized Enterprise Ecocenter (Ecocenter for short). These detectors continuously record ambient gamma radiation levels and calculate an average before transmitting that figure wirelessly (using a SkyLINK module) to a base station in an Ecocenter office in the town of Chernobyl. Those readings, transmitted once an hour, get analyzed by software and then are posted to the Ecocenter’s web site.
Santamarta considered a number of ways the data might have been manipulated: Someone could have hacked individual sensors to alter the data before it was transmitted, or intercepted and altered it while it was in transit to the base station. But this would have been too much work and been inefficient. Instead, based on the patterns, he concluded that the most likely way for someone to alter the data was to write malicious code that altered it on the Ecocenter’s server, after it was aggregated from all of the sensors.
During the period in question, forty-two sensors spiked, most of them simultaneously in clusters. To give you an idea of how the spike clusters looked, see the image below.
Radiation levels are recorded in ambient dose rates, known as microSieverts per hour (or µSv/h). This represents the amount of energy a human body would absorb from a specific level of ionizing radiation in an area. If a sensor recorded that the ambient dose rate in a particular area was .992 µSv/h, this means a human body, if exposed for an hour to the energy produced by that level of ionizing radiation, would absorb about .992 microSieverts of radiation during that hour. The acceptable exposure limit for humans for a year is 1000 µSv.
The list below shows the first spike cluster that occurred at 8:40 pm the night of February 24.


Why No Investigation?
Anyone who looks at the data and maps showing the spikes in the CEZ would likely think something was amiss. Aside from the geographical distance between spiking sensors, it should have been obvious something was wrong with the data when sensors that spiked quickly returned to normal levels.
In fact, a number of people outside Ukraine were expressing doubt about the authenticity of the data — including a radiation expert in France who told a reporter the data might have been hacked.
Yet officials in Ukraine, and at the International Atomic Energy Agency in Vienna — the United Nations body that monitors nuclear facilities around the world — didn’t investigate or even notice something was wrong with the data. Why?
The war was raging, Ukrainians were in a fight for their lives and country and were uncertain if money and military equipment would come from abroad. And staff at the Chernobyl plant were being held hostage by Russian troops. These are all good reasons why neither Ukrainian officials nor the IAEA would have taken time to notice or investigate the suspicious data patterns when they occurred. And if the IAEA suspected the data was false, this would be another reason not to become alarmed and hurry an investigation.
Yet its public statements indicated the IAEA believed the data was accurate. So why not, once Russian soldiers departed Chernobyl at the end of March, conduct an investigation then?
The IAEA sent experts to do a radiological survey in the CEZ in April, but their focus wasn’t on determining the cause of the spikes. Investigators instead wanted to determine if Russian soldiers who dug trenches in a small section of the CEZ had released dangerous levels of radiation in that area that could have sickened the soldiers or anyone else who passed through that area. (The IAEA determined the radiation levels from trench-digging could not have made the soldiers ill.) Three months later, the Ukrainian government invited Greenpeace to conduct its own radiological survey of the areas where Russian soldiers had camped, and they also did not look into the cause or veracity of the February spikes. (They concluded that the radiation levels where the soldiers camped were three times what the IAEA reported and accused the IAEA of being untrustworthy because IAEA Deputy Director Mikhail Chudakov, a Russian, is a long-term official with ROSATOM, Russia’s state atomic corporation.)
It seems strange, Santamarta told me, that both the IAEA and Greenpeace would put effort into determining if Russian soldiers were endangered from digging trenches in one small part of the CEZ and not be concerned about much higher radiation levels that sensors had recorded in other parts of the CEZ — including parts where Chernobyl staff were working.
One can understand on the surface why the IAEA might not have investigated — the agency had issued a statement after the spikes occurred saying the radiation levels had only reached 9 µSv/h, a level that posed no danger to the workers at Chernobyl or the public. But as I note in the WIRED story, the IAEA was basing this assessment on incomplete information Ukraine provided. In fact, the spikes had already reached more than 90 µSv/h by the time the agency released its statement, but the IAEA never mentioned this in its statement.
Tero Karhunen, senior inspector with Finland’s radiation and nuclear safety authority, known as STUK, told me that if ambient dose rates rise above 100 µSv/h for more than 48 hours, this normally triggers an evacuation of the affected region. The data from Chernobyl was all posted to the Ecocenter web site for everyone to see, including the IAEA, yet the agency ignored the higher numbers. Why?
Did the IAEA know or suspect the spikes were false and therefore wanted to calm the public by citing only the lower numbers? The agency wouldn’t answer any questions I sent.
The implications, if it knew or suspected the data was false and didn’t investigate, are concerning. The implications if it believed the data was accurate and told the public the radiation posed no danger to the public, when in fact 90 µSv/h did potentially pose a danger, are also concerning.
Why Did Sensor Data Stop Getting Updated?
The spikes occurred over a 14-hour period, with a number of the sensors spiking multiple times throughout this time. With some sensors that spiked more than once, the second spike was lower than the first. But other sensors that spiked more than once showed dramatic increases with the second spike — including two sensors that spiked to nearly 100 µSv/h. These two sensors, known as DGS-2 and HZHTO, initially spiked at 9:50 pm on the night of February 24 and then again at 10:40 am the next morning.
DGS-2 (which normally recorded a radiation dose level of 7.67 µSv/h) spiked to 58.8 µSv/h at 9:50 pm on February 24th, and then to 93 µSv/h at 10:40 am the next morning. And HZHTO (which normally recorded a radiation dose level of 2.98 µSv/h spiked to 65.5 µSv/h at 9:50 pm and then to 93 at 10:40 am the next morning.
Both DGS-2 and HZHTO got very close to 100 µSv/h — the level which Karhunen says generally triggers an evacuation if it lasts for 48 hours. Given the upward trajectory of the spikes between 9:40 pm and 10:50 am, it’s possible they would have climbed higher with subsequent spikes. We’ll never know if they would have reached higher levels, however, because the Ecocenter’s online map stopped updating data after 10:50 am on February 25th. This meant nuclear experts outside Ukraine, and others who were monitoring the Ecocenter web site to track the radiation levels in the CEZ, were suddenly blind to what was occurring there.

It’s not clear why the data suddenly stopped, but there are a couple of possibilities. The following is speculation.
- Ukraine was experiencing intermittent internet and electricity outages on the day of the invasion, and it’s possible the Ecocenter’s internet service went out. In this case, the radiation sensors in the CEZ would still have recorded radiation levels (they are battery operated after all) and they still would have transmitted the data to the Ecocenter base station. With the internet out, however, the data could not get posted to the Ecocenter’s web site. But once internet connectivity was restored, data held in reserve should have posted. Indeed, data from the sensors all came back online the following Monday, February 28 (at this point they were all reporting normal radiation levels again). The sensors all went offine again by March 3, however, and remained that way until long after Russian soldiers ended their occupation of the Chernobyl plant and CEZ.
- But there’s an alternate theory. If internet outages didn’t prevent the data from getting uploaded to the Ecocenter web site, and the sensors themselves were still recording and transmitting data, there is a possibility that someone pulled the plug on the Ecocenter server that was used to process and upload the data to the web site. Ukrainian authorities say that Russian soldiers at the Ecocenter’s office in Chernobyl stole the hard drive from the server used to process the radiation data, but couldn’t say when that occurred — on March 3 when the web site stopped posting data or later as the soldiers were departing Chernobyl. If they stole it on March 3, this could explain why the data stopped updating. But if they stole it later than this, then this doesn’t explain why data stopped updating to the web site. And it suggests that somene intentionally stopped the data from posting — possibly because they knew the data was false and feared that radiation levels higher than 100 µSv/h would get posted to the web site and cause panic.
- There’s another mystery, however. Ordinarily the Ecocenter’s system automatically transmits the sensor data to the IAEA around the same time it’s posted to the Ecocenter’s online map. But at some point on February 24, the IAEA stopped receiving this direct data transmission, even though data continued to get updated to the Ecocenter’s web site until February 25th, and then again on the 28th when all of the sensor data came back online. Did someone know the data was false and halt the transmission to prevent the IAEA from acting on false data if the levels increased to 100 µSv/h? There are a lot of unanswered questions.
Two Ways to Verify the Data

The GammaTRACERs store data in their memory. This data could be used to verify if the data the Ecocenter posted to its web site was accurate. If someone had altered the data on the Ecocenter server, it wouldn’t match the data stored in the memory of the sensors. The memory of these devices only hold so much data, however, before it’s overwritten, and it’s not clear if the data from February 2022 still remains in them.
In addition to the digital GammaTRACERs that measure energy produced by ionizing radiation, some of the sensor stations also have an aerosol filter that measures ambient dose levels in the air. These filters are much more sensitive to radiation changes than the digital sensors and therefore are more accurate in detecting radiation dose levels. The filters would have been a great way for Ukraine to verify that the levels recorded by the GammaTRACERs were accurate.
Prior to the invasion, Chernobyl workers would collect these filters once a week to test them in a lab. But during the occupation of Chernobyl, it appears workers were prevented from collecting and testing the filters. Once Russian soldiers left Chernobyl and the CEZ, however, it would have been a great time for workers to collect the filters and test them. Unfortunately, according to a nuclear expert from Greenpeace who entered the CEZ a few months after the Russians left, there were landmines littered throughout the CEZ and it would have been dangerous for workers to collect the filters. It’s unclear if the filters have been collected since then.
One other way to verify the accuracy of the sensor data — either after the Russians left or today — would be to do a forensic investigation of the sensors themselves and the Ecocenter server used to process and publish the data online. Unfortunately, the Ecocenter server — or its hard drive — is gone. According to Ukrainian authorities, the Russians took it. They also took specialized software used to process and analyze the sensor data.
What Happened to the Server?
The server is an important piece of the puzzle and could help determine if someone manipulated the sensor data. The Ukrainians say that Russian soldiers absconded with the entire server when they left Chernobyl. Workers at the Ecocenter even appeared to show a French TV station the empty cabinet where the server had been stored.

When I asked Ukrainian authorities in charge of the Ecocenter lab what the Russians took from that facility, they told me they didn’t take entire components. Instead they only took parts, such as hard drives.
“Most computers [were] stolen not in assembled form (such as a monoblock, laptop, or system unit), but in disassembled form, as parts,” Maksym Shevchuk, deputy head of the State Agency for the Management of the Exclusion ZoneIn — which oversees the Ecocenter — told me in an email. “The Russian occupiers stole many hard drives of computers, and the rest of their components were scattered around the offices and territory of the nuclear power plant.”
Here’s are photos showing some of the damage left behind by Russian soldiers at Chernobyl. The images were provided to me by the State Agency for the Management of the Exclusion Zone.


Why would the Russians remove hard drives and not the entire towers? Perhaps the answer is as simple as space. They didn’t have enough space in their military vehicles to carry entire computer towers back to Russia, so they just took the hard drives. But why take the hard drives?
Who and Why - A Speculative Exercise
If the radiation data at Chernobyl was manipulated, this raises questions about who had the means to do it and why. As I note in the WIRED story, there are two obvious possibilities — Russia and Ukraine — both of whom had means and motive, both of whom had access to the Ecocenter server and radiation sensor data.
It makes sense to consider what occurred from the viewpoint of either scenario, though all we can do is speculate at this point.
If Russia falsified the data as part of a disinformation campaign, as I discuss in the WIRED story, to bolster its claims that Ukraine was building a dirty bomb at Chernobyl, then it would have made sense if Ukrainian workers at Ecocenter grew alarmed by the spikes and pulled the plug on the server to thwart the disinformation campaign. But once Russian soldiers had control of the Ecocenter facilities, why remove the hard drives? To remove evidence of Russia’s manipulation?
If Ukraine was responsible for manipulating the data and falsifying the radiation spikes — to alarm the West or control the movement of Russian soldiers at Chernobyl, as I discuss in the WIRED story — the scenario becomes more interesting. If workers at Chernobyl created the spikes, and someone in authority realized the implications of deceiving the IAEA and the public with false data and ordered them to stop, this could explain why the data suddenly stopped transmitting to the IAEA and stopped being updated to the Ecocenter web site. Alternatively, Russia could have realized that Ukraine was falsifying the data to drum up support from Europe and the US by showing that the invasion had created a dangrous nuclear risk and ordered soldiers at Chernobyl to seize the Ecocenter hard drives to halt the Ukrainian disinformation campaign. Who knows?
Without an investigation, we may never know the truth.
Shevchuk told me in an email that his agency would consider investigating the radiation spikes if merited, but would do so only after the war has ended. With the Ecocenter hard drives missing, and the unlikelihood that any 2022 data in the memory of the GammaTRACERs would still remain at the end of the war, it’s not clear an investigation would even be possible.
The mystery of Chernobyl may remain a mystery.
Thank you for reading. If you found this article useful or interesting, feel free to share it with others.
Zero Day is a reader-supported publication. You can support my work by becoming a paid subscriber; or if you prefer, you can subscribe for free:
You can also give a gift subscription to someone else: